Smartphone-based decentralized confidential compute venture Acurast has raised $11 million, claiming tamper-resistant execution on shopper telephones and safe {hardware} verification.
In accordance with a Thursday announcement shared with Cointelegraph, Acurast raised $11 million from Ethereum co-founder and Polkadot founder Gavin Wooden, MN Capital founder Michael van de Poppe and GlueNet founder Ogle, amongst others. The venture goals to launch its mainnet on Nov. 17, and plans to launch its native token ACU alongside it.
Acurast founder Alessandro De Carli stated “billions of smartphones are probably the most battle-tested {hardware} on earth” and that the corporate hopes to cut back prices by leveraging them for “verifiable, confidential compute.”
The community explorer stories that just about 150,000 telephones have already joined the community and processed over 494 million transactions, enabling the deployment of virtually 94,200 companies.
“We take away the gatekeepers, scale back the prices, and convey safe, trustless computation to anybody, anyplace, and all and not using a knowledge middle,” De Carli claimed.

Acurast community knowledge. Supply: Acurast
Associated: Decentralized compute networks will democratize world AI entry
Confidential compute on third-party {hardware}?
Acurast says it allows confidential computing — the place customers with bodily entry to smartphones working the node software program can not entry the information used for computation — to be offered by anybody. This requires a setup that ensures, to a excessive diploma of certainty, that the smartphone’s proprietor can not alter the software program in a approach that compromises this secrecy.
To this finish, the venture’s builders applied a collection of checks to make sure that the smartphone is working manufacturer-approved software program that might not compromise its safety assumptions. Nonetheless, related measures have been applied by banking app builders for a few years, just for communities of customized firmware comparable to Graphene OS to search out workarounds that enable them to run the functions on their non-sanctioned setups. De Carli stated that this doesn’t apply to Acurast’s app.
De Carli instructed Cointelegraph that the Acurast processor software sends hardware-backed key pairs with key attestation to the Acurast protocol. If these don’t match these offered by the smartphone producer, “the Acurast processor shouldn’t be capable of get a sound attestation, thus can not take part within the community.”
De Carli stated that “this ensures solely real and attested {hardware} could be onboarded” and unsuitable environments “can’t be onboarded, as a result of they don’t get the signed attestation connected to their keys,” that means the telephone’s proprietor can not tamper with person knowledge or the execution setting.
Associated: Dubai strikes to manage machine economic system with DePIN peaq community
The safety limitations
Nonetheless, the safety assumption breaks if a manufacturer-endorsed smartphone working system — iOS or Android — is exploited in the appropriate approach by malware or its rightful proprietor.
De Carli largely dismissed the notion, saying that “should you handle to search out an exploit that permits you to take action, you successfully are eligible for a multimillion-dollar bounty and the exploit could be mounted shortly thereafter” — pointing to Google’s bug bounty program for example.
Nonetheless, previously, such vulnerabilities had been certainly found.
As an example, in Samsung’s TrustZone Working System, a keymaster AES-GCM IV-reuse assault was found in 2022, which allowed protected key extraction and abuse of attestation. Moreover, an attacker who has already compromised the app course of or the kernel will doubtless be capable to encrypt and decrypt content material, however gained’t be capable to extract the non-public key itself.
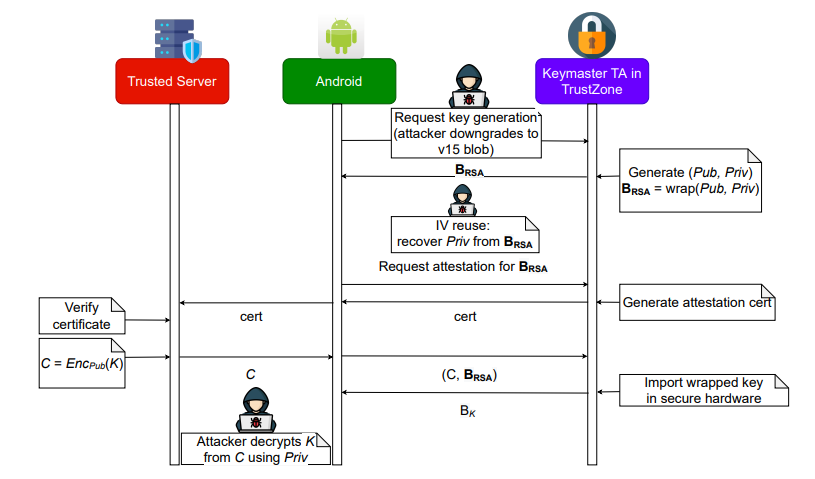
AES-GCM IV-reuse assault. Supply: USENIX
Journal: Blockchain’s subsequent huge breakthroughs: What to look at